MODERN DATABASE SECURITY MODEL:
Dynamic and Precise Protection for your Data
Reduce risk with Fauna’s enterprise security & compliance solutions built for modern applications



Introduction to Fauna Security
Explore Fauna's robust security features in 5 minutes: From encryption and access controls to comprehensive data compliance, Fauna ensures your data remains secure at every level.

Reduce Risk
Fauna enhances security by supporting both dynamic Attribute-Based Access Control (ABAC) and Role-Based Access Control (RBAC) – providing flexible, fine-grained access control tailored to user attributes and roles. ABAC allows real-time adjustment of access rights based on precise, attribute-specific criteria – ensuring each transaction adheres to the principle of least privilege, significantly minimizing blast radius in the event of a breach.
Automated Resilience and Compliance
With Fauna, data is automatically replicated to multiple locations to ensure data can be served even in the event of a full regional outage. Designed to meet stringent data protection standards like GDPR and HIPAA, Fauna provides streamlined compliance and robust data protection.
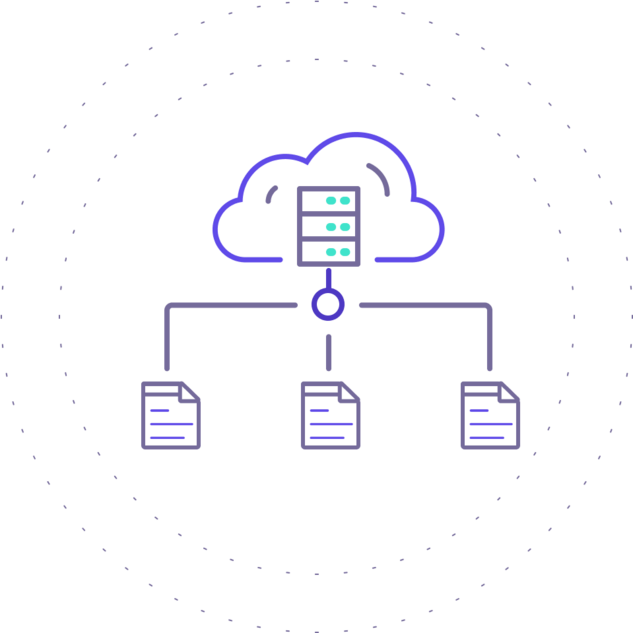
Increase Operational Efficiency
Traditional databases often require third-party solutions and extensive operational overhead for fine-grained authorization, data isolation, and other security measures. Fauna offers robust and modern security features natively, eliminating the need for additional tools and reducing operational complexity.
“Fauna is the reason we are still in business. There is not enough good stuff I can say about the folks over there.” Read case study

Alice
From Wonderland

Capabilities
Ready to ship apps faster? Start today.

Authentication
Fauna offers a versatile and secure authentication system to meet various needs.
Every transaction in Fauna is an independently secured HTTP API request authenticated using secrets. Secrets can be passed as bearer tokens and are scoped to a specific database or an account’s top-level context. They are used for both routing requests and authorization, with each secret potentially having one or more roles to control data access. Fauna keys offer anonymous access to specific resources in your database without being tied to a specific identity. Tokens, meanwhile, provide a secure method for identity-based access to your database, allowing users, services, systems, or processes to run queries with specified privileges, supporting dynamic ABAC.
Fauna also seamlessly integrates with external identity providers, allowing you to leverage existing authentication systems for streamlined user access management.

Authorization
With Fauna’s RBAC, you assign predefined roles with static privileges. If an authentication secret has a role, it’s granted all of the role’s privileges.
Meanwhile, you can dynamically assign roles to JWT’s and Tokens leveraging Fauna’s Dynamic ABAC, which extends beyond traditional static policies by enabling real-time, data-driven application of business logic to control access based on the user or system requesting access, the resource being accessed, the operation, and the environment. ABAC policies can be implemented across three layers:

Data ABAC: Controls access at the document level, based on predefined permissions within the documents.

Identity ABAC: Manages access based on the user's identity.

Query ABAC: Confirms user access rights by correlating the identity with relevant data tables.


Data ABAC: Controls access at the document level, based on predefined permissions within the documents.

Identity ABAC: Manages access based on the user's identity.

Query ABAC: Confirms user access rights by correlating the identity with relevant data tables.

Virtual Private Fauna
Fauna’s single-tenant offering, is fully customizable to meet your specific security and compliance needs. It can be configured across a single region, multiple regions, and/or multiple clouds while maintaining Fauna’s fully serverless, API delivery model.



Data Encryption
To protect data in transit between users and Fauna servers, Fauna uses Transport Layer Security (TLS) version 1.2 or better, creating a secure data transmission method protected by 128-bit or higher Advanced Encryption Standard (AES) encryption. Connections to the service that do not utilize this level of encryption are not permitted. Data uploaded to the Fauna service is encrypted at rest.


Database multi-tenancy
By leveraging Fauna's built-in hierarchical, parent-child database structure for multi-tenancy, businesses can ensure robust data isolation for each tenant. Unlike traditional databases that use a tenant column in the same table and filter queries, or mandate managing separate databases, configurations, and security protocols for each tenant, Fauna's model prevents any risk of cross-tenant data access, providing stronger guarantees for data security and integrity while also simplifying management operations and cutting costs.


Private Endpoints
Fauna offers Private Endpoints, enabling secure VPC peering directly from your AWS, GCP, or Azure environments, ensuring traffic between your VPC clients and Fauna isn’t exposed to the Internet or other public networks.


Query Logs and Backups
Track access patterns and gain visibility to system changes across specified time intervals through Fauna’s Query Logs. Meanwhile, Fauna’s Backup & Restore system ensures that your database can be restored in the event of an account compromise by malicious actors, offering configurable snapshot frequencies and retention periods for optimal security.

Build Applications with Confidence
Strict Authorization Requirements
Fauna's Attribute-Based Access Control (ABAC) limits the blast radius in the event of a breach by enabling fine-grained access controls that can dynamically adjust permissions based on user attributes and context. This reduces the risk of extensive data exposure and enhances security by ensuring only the necessary data is accessible to each user. This is crucial for businesses that prioritize safeguarding sensitive data and maintaining operational integrity, particularly in sectors like finance and healthcare.


Secure Data Transaction Requirements
Fauna’s stateless connectivity model, which operates over HTTPS, ensures that each transaction is secure and isolated. This model eliminates the risks associated with stateful connections by ensuring that each query is independently authenticated and authorized without relying on persistent connections.
Data Redundancy and Compliance Requirements
With Fauna's built-in data redundancy and secure backup capabilities, businesses can safeguard against data loss due to system failures, operational errors, or cyberattacks. Fauna ensures that multiple copies of data are maintained within defined region groups and offers configurable backup frequencies and retention policies to meet compliance and business continuity requirements.


Multi-Tenant Data Isolation Requirements
Fauna provides robust multi-tenancy capabilities that ensure strict data isolation between tenants. This is crucial for organizations that manage data across multiple clients or departments and need to prevent unauthorized access or data leaks between them. By integrating data isolation into the database system itself, Fauna helps organizations maintain high levels of security and compliance without the need for complex external solutions.
Build Applications with Confidence
Strict Authorization Requirements
Fauna's Attribute-Based Access Control (ABAC) limits the blast radius in the event of a breach by enabling fine-grained access controls that can dynamically adjust permissions based on user attributes and context. This reduces the risk of extensive data exposure and enhances security by ensuring only the necessary data is accessible to each user. This is crucial for businesses that prioritize safeguarding sensitive data and maintaining operational integrity, particularly in sectors like finance and healthcare.


Secure Data Transaction Requirements
Fauna’s stateless connectivity model, which operates over HTTPS, ensures that each transaction is secure and isolated. This model eliminates the risks associated with stateful connections by ensuring that each query is independently authenticated and authorized without relying on persistent connections.
Data Redundancy and Compliance Requirements
With Fauna's built-in data redundancy and secure backup capabilities, businesses can safeguard against data loss due to system failures, operational errors, or cyberattacks. Fauna ensures that multiple copies of data are maintained within defined region groups and offers configurable backup frequencies and retention policies to meet compliance and business continuity requirements.


Multi-Tenant Data Isolation Requirements
Fauna provides robust multi-tenancy capabilities that ensure strict data isolation between tenants. This is crucial for organizations that manage data across multiple clients or departments and need to prevent unauthorized access or data leaks between them. By integrating data isolation into the database system itself, Fauna helps organizations maintain high levels of security and compliance without the need for complex external solutions.

Get started building with Fauna
Explore resources that can help get you up and running in minutes.
Multi-tenant SaaS Sample App
Learn how to build a multi-tenant, multi-region SaaS app without ops using Fauna and AWS
BUILD THE SAMPLE APP
New to Fauna Query Language?
This guide can help you get started with FQL in under 10 minutes.
READ MORE
Workshops
Learn how to build complete applications using technology like AWS, Cloudflare, and more.
EXPLORE THE WORKSHOPS
FAQs
Ready to get started?
Launch a new app, modernize an existing app, and scale seamlessly across regions.
Ready to get started? Launch a new app, modernize an existing app, and scale seamlessly across regions with FQL.